My research on how AI has been weaponized is chilling, but I’ve come to realize that AI is only useful when accessing the massive data on the internet. An internet that we’ve been herded onto, for everything we do in our modern lives.
Maybe that was the plan all along?

In Surveillance Valley, Yasha Levine reminds us that: “The Internet was hardwired to be a surveillance tool from the start. No matter what we use the network for today–dating, directions, en-crypted chat, e-mail, or just reading the news–it has always had a dual-use nature rooted in intelligence gathering and war…The Internet is the most effective weapon the government has ever built.”
AI plus the internet is how Israel was able to attack Hezbollah in Lebanon even as the resistance organization operated with the strictest operational security. Hezbollah commanders and fighters were targeted and eliminated because while revolutionaries must operate in a sea of supporters, in our modern internet age the supporters meta-data can give them away. Intelligence agencies like Mossad and Unit 8200 are now using archived data, reconstructing entire timelines from past internet activity. What makes this especially lethal is not any one data point but the combination. Signals collected by drones are combined with metadata, AI analysis, ground informants, and environmental profiling. From all of these inputs, a kill matrix can be developed.
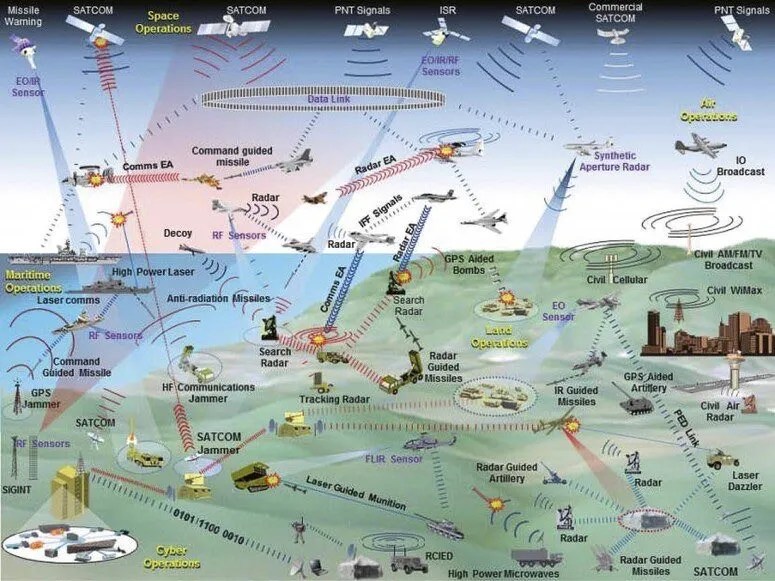
In a nod to the CIA’s Phoenix Program, Israel in September 2024 detonated thousands of booby-trapped pagers and walkie-talkies that had been covertly distributed among Hezbollah’s civilian cadres. The devices exploded simultaneously across Lebanon, killing dozens and maiming thousands. It was a devastating act of remote sabotage, designed not only to eliminate personnel, but to sow mistrust in Hezbollah’s means of communication. Soon after Israel bombed Hezbollah’s Beirut headquarters located 60 feet underground beneath residential buildings in the Dahieh suburb, killing Hassan Nasrallah, the secretary-general and many other key Hezbollah commanders. The Israeli Air Force attacked the buried command post using 2000 pound bunker-buster bombs, guided unerringly by the AI kill matrix. The latest breach of Hezbollah’s operational environment marks a technological leap that fundamentally alters the rules of engagement, where Israels war on the resistance movement has been fought using AI to monitor phones, undersea cables and the internet.
In Israel’s silent war on Lebanon, Mohamad Shams Eddine, calls the model of infiltration: Environmental Fingerprint Profiling (EFP). And how it’s the most lethal vulnerability facing any resistance movement embedded in a civilian society. “To grasp how commanders are now being reached inside Hezbollah’s fortified operational circles, one must first understand the layered technological arsenal deployed against them. The breach emerges from the fusion of dozens of surveillance systems into a unified, real-time data engine. In the past, hacking meant breaching a phone or computer. Today, the paradigm has shifted. The new target is not the device itself, but the digital ecosystem surrounding it. Israeli intelligence no longer needs to penetrate Hezbollah devices directly. They monitor the people around the target, the signals emitted by their environment, and the data shared unwittingly by family, friends, or even neighbours. A commander might carry a phone with no internet access, avoid public networks, and live free of digital identifiers. It doesn’t matter. Surveillance focuses on his driver, whose smartphone logs every route. The building Wi-Fi silently confirms presence. Smart cars track speed, location, and habits. Street cameras catch his face; apps map who else is nearby. As a result, the target’s own environment becomes compromised.”

It’s clear that what Israel and US tech companies like Palantir are doing has already been imported to the homeland. There’s a link between Palantir tools used by ICE and those used by the IDF in Gaza: ISTAR technology (short for Intelligence, Surveillance, Target Acquisition and Reconnaissance) AI tools that harvest and weaponize people’s data in war. While the Chairman of the Joint Chiefs of Staff suggests that we’ll see more military force used in American neighborhoods and as the Department of Defense calls artificial intelligence “America’s next manifest destiny.” The surveillance regime that Silicon Valley has helped control Gaza now extends far beyond the Middle East, as ISTAR tools become commonplace in our country.
Surveil, control and murder–coming to a locale near you.

Already, Americans are increasingly subjected to the watchful eye of AI surveillance and drones in cities across the country — including Denver, LA, and Chicago — with minimal understanding of how these systems work, often in secret and without democratic consent. Palantir’s CEO publicly talks about killing people, and has fantasized about poisoning critics using covert methods such as fentanyl-laced drone strikes. Palantir’s executives are also vocal about wanting to flex the definition of terrorism to include their enemies, as Palantir’s Defense chief Mike Gallagher did on Fox News when he called for the feminist group Code Pink to be classified as domestic terrorists.
Meanwhile, Trump is Building a Massive Data Center Beneath the East Wing. Israel built a fortified, 9 story deep, AI surveillance, targeting and operational decision-making command post. Trump is following suit. Remember, on January 21st, 2025, Trump’s first full day in office, they launched Project Stargate, a $500 billion AI infrastructure project, that was never really explained.
I wonder why?
The vast amounts of data that we feed into the internet–about our lives, our location, our relationships, and our plans–can be used against us in ways we might not yet imagine. It is in the interest of many defense-tech companies like Palantir to help their clients figure out crueler and crueler ways to have AI do so. We can see the powers of the world merging: corporate power, state power, institutional power, ideological power, the power of the oligarchs who built and control the internet, the power of the network itself. Some days it can feel as if we are living inside the plot of a piece of twentieth-century dystopian sci-fi.
Any serious revolutionary movement will have to destroy or block the internet. It was sold as transformative technology that would allow for connectivity and freedom but recent actions by our dystopian empire have shown that was a pipe dream. Perhaps the authorities always saw this outcome or maybe it’s AI that makes the surveillance so much better. Precision targeting depends on data collected from communication devices, GPS, and facial and voice recognition. Only AI can correlate such seemingly unrelated data points at lightning speed to pinpoint a target’s exact presence. This is the age of algorithmic warfare. And no resistance can afford to ignore it.
In the 1960’s activists called for Americans to kill their televisions.
Maybe it’s time to kill the internet?
Update: The internet is useful for insurgency, as well as counterinsurgency. In Iran, for example, the CIA and Mossad have deployed Starlink terminals to help affect regime change. But now the Iranian government, with the aid of Russian and Chinese tech, has jammed the Starlink terminals. Without internet access the CIA/Mossad agents directing the rioters are unable to command and control their on-the-ground forces. The lack of ‘horror’ propaganda videos from Iran, submitted via the internet and used by the media to maintain support for intervention, is also important.
